Best Remote IoT: Raspberry Pi Behind Router Guide
Are you ready to unlock the full potential of your Raspberry Pi, transforming it into a powerful remote access hub? This guide will provide a comprehensive roadmap, ensuring seamless connectivity and secure access to your Raspberry Pi, no matter where you are, behind any router.
The realm of the Internet of Things (IoT) is rapidly expanding, and with it, the need for robust remote access solutions is paramount. Whether you're a seasoned developer, a curious hobbyist, or a professional seeking to streamline your projects, the ability to remotely control and monitor your Raspberry Pi opens up a world of possibilities. Imagine managing your home automation system from across the globe, troubleshooting a remote sensor, or accessing critical data from your IoT projects with ease. This comprehensive guide will walk you through the intricacies of setting up the best remote IoT system, ensuring you can access your Raspberry Pi behind a router and firewall, without compromising security or functionality.
The challenges of establishing remote access often revolve around overcoming the barriers posed by routers and firewalls. These network gateways, while essential for security, can hinder direct connections to devices within your local network. However, with the right tools and configurations, you can circumvent these obstacles and establish a secure and reliable connection to your Raspberry Pi from anywhere. This article will explore the best practices, tools, and configurations, offering a step-by-step approach to setting up remote IoT operations, whether you're looking for free solutions or considering advanced services.
- Snoop Doggs Father Vernell Varnados Life Influence
- Alice Rosenblum Exclusive Content Leaks What You Need To Know
This comprehensive guide dives deep into the critical aspects of remote access. We will explore the importance of proper router configuration, the role of tools like ngrok and reverse SSH tunnels, and the benefits of using a dynamic DNS (DDNS) service. We will also delve into the best practices to ensure seamless connectivity, security, and functionality. The ultimate goal is to empower you with the knowledge and tools to create a robust and secure remote IoT setup, making your Raspberry Pi accessible from anywhere in the world.
| Feature | Details |
|---|---|
| Topic | Best Remote IoT Solutions for Raspberry Pi Behind a Router |
| Core Concept | Enabling secure and seamless remote access to a Raspberry Pi, managing IoT devices, and accessing your projects from anywhere in the world, even behind a router. |
| Key Benefits |
|
| Target Audience | Hobbyists, Students, Professionals, Developers, anyone who wants to manage and use their Raspberry Pi remotely, and also anyone interested in IoT and Home Automation. |
| Relevant Technologies | Raspberry Pi, SSH, Port Forwarding, Dynamic DNS (DDNS), ngrok, Reverse SSH Tunnels, Raspberry Pi OS, Firewalls, Routers |
| Tools and Strategies | Router Configuration (Port Forwarding, UPnP), SSH key authentication, Dynamic DNS, reverse SSH tunnels, and Secure Shell access. |
| Expected Outcomes |
|
| Reference | Official Raspberry Pi Foundation Website |
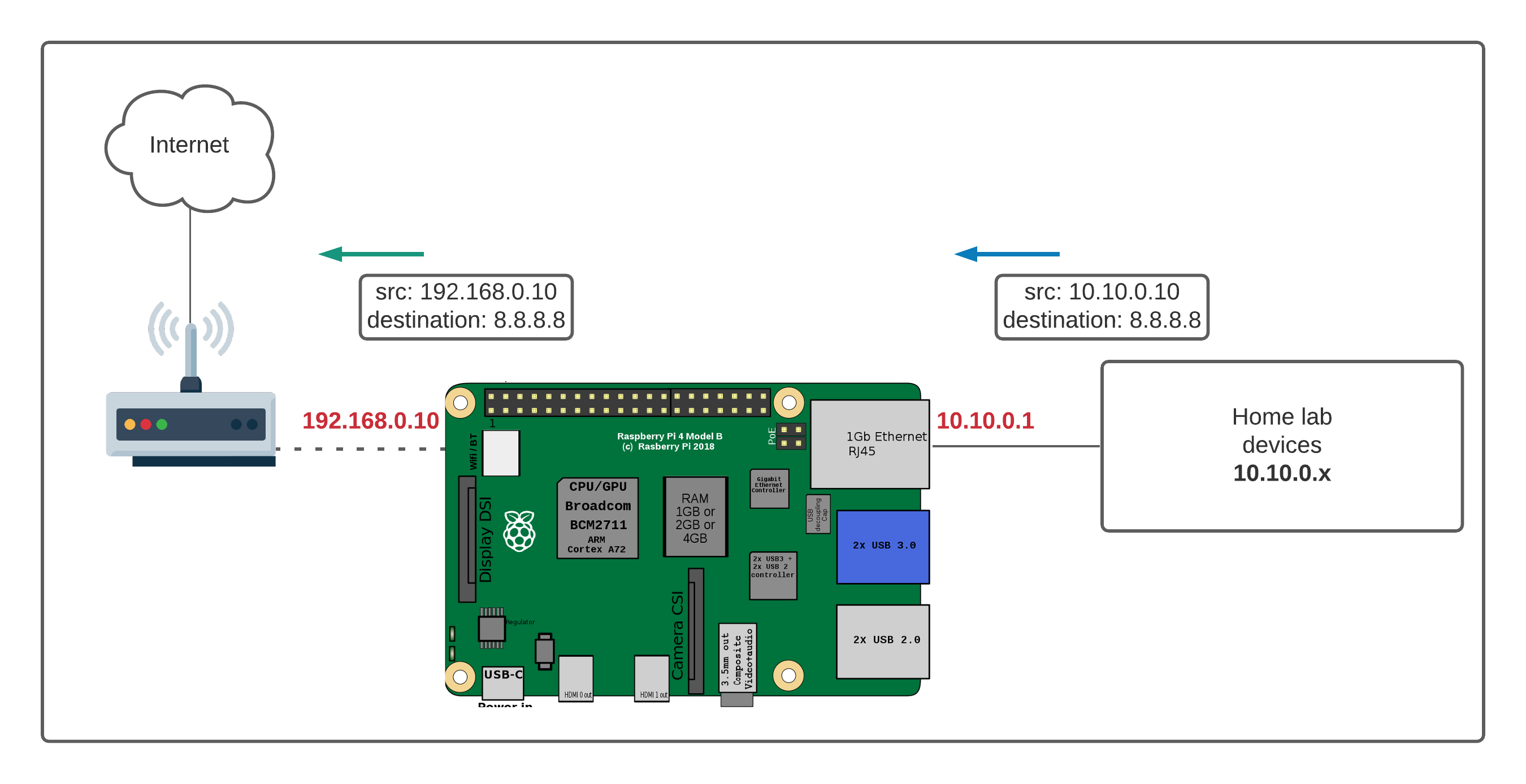
Before diving into the specifics, it's essential to understand the foundational elements. The Raspberry Pi, a credit-card-sized computer, serves as the brain of your remote IoT hub. Its versatility and affordability make it ideal for a wide range of applications, from home automation to environmental monitoring. Your router, acting as a gateway to the internet, presents a barrier to direct connections. However, with the right configuration, you can instruct the router to forward incoming traffic to your Raspberry Pi. This process, known as port forwarding, is a critical first step.
The journey to seamless remote access involves more than just port forwarding. You'll also need to consider security. Employing secure shell (SSH) is a cornerstone of this security. SSH allows you to establish an encrypted connection to your Raspberry Pi, protecting your data from eavesdropping. Further enhancing security, consider using SSH key authentication instead of password-based logins. This method involves generating a key pair (a private key that you keep secure and a public key that you install on your Raspberry Pi). When you connect, your computer uses the private key to "prove" it has the right to access the Pi, providing a significantly more robust and secure method than a password.
- Alice Rosenblum Unveiling Leaks Onlyfans More Latest Info
- Alice Rosenblum Leaks What You Need To Know Updates
The concept of dynamic DNS (DDNS) is another vital component. Most internet service providers (ISPs) assign dynamic IP addresses to your router. This means your public IP address can change periodically, making it difficult to maintain a consistent connection. DDNS services, such as DuckDNS or No-IP, solve this problem by associating a static hostname with your dynamic IP address. This way, you can always connect to your Raspberry Pi using the same hostname, regardless of its changing IP address. Configuring a DDNS service on your Raspberry Pi and router simplifies remote access and eliminates the need to constantly track your IP address.
For those seeking simpler solutions, services like ngrok offer a straightforward way to expose your Raspberry Pi to the internet. Ngrok creates a secure tunnel, allowing you to bypass complex router configurations. It provides a temporary public URL that you can use to access your Raspberry Pi. While convenient, its essential to understand the security implications and use these services responsibly. Ngrok can be a great tool for testing and prototyping, but for long-term deployments, you should consider the costs and limitations, especially regarding the temporary nature of the URL in the free version.
Another advanced technique involves using reverse SSH tunnels. This method allows your Raspberry Pi to initiate a connection to a remote server, which then acts as a gateway, allowing you to access your Pi even if your router blocks incoming connections. This is particularly useful when you cant directly configure your router, such as when you are behind a restricted network. Setting up reverse SSH tunnels can be slightly more complex than port forwarding but can offer enhanced security and flexibility, especially in environments with strict network restrictions.
The process of setting up remote access typically involves several key steps. First, you must configure your router. This usually involves accessing your routers administration panel through a web browser. You'll need to identify your Raspberry Pi's local IP address, which can be found through your router's DHCP client list or by checking the Raspberry Pis network settings. Then, you'll need to create a port forwarding rule that directs incoming traffic on a specific port (e.g., port 22 for SSH) to your Raspberry Pis IP address and port. Its also recommended to reserve a static IP address for your Raspberry Pi in your router settings, so its IP address doesn't change, preventing you from having to reconfigure your port forwarding rules.
With port forwarding configured, the next step is to set up SSH access. On your Raspberry Pi, ensure the SSH server is enabled. You can typically verify this by using the `sudo systemctl status ssh` command. If its not running, you can start it with `sudo systemctl start ssh`. For security, change the default SSH port from 22 to a different, less commonly used port. This is a basic security measure that makes it slightly harder for automated attacks to find your SSH server. Then, configure SSH key authentication. Generate a key pair on your local machine and copy the public key to the Raspberry Pis `~/.ssh/authorized_keys` file.
Once SSH is properly set up, install and configure a DDNS client, such as `ddclient`, on your Raspberry Pi. Youll need to sign up for a DDNS service and obtain your account credentials. Configure the client with your DDNS provider's details, your hostname, and your login information. The client will automatically update your DDNS record whenever your public IP address changes. After all of that, test your configuration by trying to SSH into your Raspberry Pi using your DDNS hostname.
For those seeking simplicity, consider services like ngrok. Install the ngrok client on your Raspberry Pi, and then authenticate it using your ngrok account token. Use the `ngrok tcp 22` command to create a tunnel for SSH access (or the appropriate port for other services). Ngrok will provide you with a temporary public address that you can use to access your Raspberry Pi. While convenient, always consider the potential security risks of relying on a third-party service.
When setting up reverse SSH tunnels, you'll need a server with a public IP address that you can connect to. This could be a virtual private server (VPS) or another Raspberry Pi located on a network with a public IP address. On your Raspberry Pi, run a command like `ssh -R 2222:localhost:22 user@remote_server_ip` to create a reverse tunnel, where `2222` is a port on the remote server to connect to your local port 22 (SSH). Then, connect to the remote server and access your Raspberry Pi via `ssh localhost -p 2222`. This provides a secure pathway for you to access your Raspberry Pi even through firewalls.
Security should be a constant concern. Regularly update your Raspberry Pi's operating system and software packages. This can be done with the commands `sudo apt update` and `sudo apt upgrade`. Use strong, unique passwords, or better yet, rely on SSH key authentication. If possible, enable a firewall on your Raspberry Pi to restrict access to only the necessary ports and IP addresses. Consider implementing two-factor authentication (2FA) for added security, if possible. Regularly audit your system logs to detect any suspicious activity.
Beyond basic SSH and port forwarding, consider more advanced security measures. Install and configure a firewall, such as `ufw` (Uncomplicated Firewall), on your Raspberry Pi. This allows you to control the incoming and outgoing network traffic. Restrict access to SSH to only known IP addresses. Configure fail2ban to automatically block IP addresses that repeatedly fail to authenticate. Implement intrusion detection systems (IDS) to monitor your network traffic for malicious activity. These measures can significantly enhance the security of your remote access setup.
The choice of the best solution largely depends on your specific needs and technical expertise. Port forwarding combined with DDNS and SSH key authentication offers a solid, free, and secure solution for most users. Ngrok offers an easy-to-use, temporary solution, suitable for testing and prototyping. Reverse SSH tunnels offer robust solutions for situations where router configuration isn't feasible. Evaluate your needs, consider the pros and cons of each method, and choose the one that best fits your technical skills, your budget, and your specific project requirements.
When choosing tools, prioritize security, ease of use, and cost-effectiveness. A combination of the Raspberry Pi OS, SSH, and a free DDNS service, along with SSH key authentication, provides a powerful and cost-effective solution. If ease of use and rapid deployment are paramount, ngrok offers a simpler experience. Evaluate the capabilities of each tool, and choose the one that aligns with your overall goals.
Setting up remote SSH IoT behind a router with a Raspberry Pi is a valuable skill set. It enables access to manage your IoT devices, monitor projects, or control home automation. By following the strategies outlined above, you can establish seamless and secure connectivity, opening a world of opportunities. Whether you're managing devices, on vacation, or simply want to monitor the status of your devices, remote access can transform your projects.
The best remote IoT setup is the one that meets your needs. By implementing secure configurations and leveraging the features of Raspberry Pi, SSH, DDNS services, and other tools, you can create a robust system that will empower you to manage your IoT projects and access your devices from anywhere. Remember to keep your system updated, implement strong security measures, and monitor your network. With these best practices, you can enjoy the convenience of remote access without compromising the security of your devices. Your ability to remotely access your Raspberry Pi can revolutionize how you manage remote devices and IoT projects.
In conclusion, setting up the best remote IoT behind a router with a Raspberry Pi is an achievable goal. With the proper configuration, a little bit of technical knowledge, and a focus on security, you can enjoy all the benefits of remote access, from anywhere in the world. The key is to understand the fundamentals of networking, the capabilities of your Raspberry Pi, and the power of the tools at your disposal. Remember to prioritize security, stay updated, and experiment with different methods until you find the setup that's perfect for your needs. The world of remote IoT awaits!


Detail Author:
- Name : Vincent Emmerich
- Username : omccullough
- Email : guadalupe07@gmail.com
- Birthdate : 1974-04-22
- Address : 19519 Robel Hollow Apt. 548 Vitaview, IL 61132-0650
- Phone : 1-862-981-3764
- Company : Kemmer Inc
- Job : Psychiatric Technician
- Bio : Rem provident non consequatur. Magni inventore veritatis eum enim id numquam. Ipsum illum natus officia ut rerum. Cupiditate consequatur incidunt quisquam corrupti.
Socials
instagram:
- url : https://instagram.com/cloyd_id
- username : cloyd_id
- bio : Placeat blanditiis aliquam nam occaecati est quae. Dolor autem dolorum totam harum.
- followers : 3017
- following : 751
twitter:
- url : https://twitter.com/cloyd_official
- username : cloyd_official
- bio : Eius sequi sint ut qui quo est. Quia accusamus quia ratione minima. Ea enim libero ut harum. Ut explicabo pariatur eum dolorum exercitationem.
- followers : 3668
- following : 42
facebook:
- url : https://facebook.com/sawayn2006
- username : sawayn2006
- bio : Quas voluptatem quas libero ratione quis.
- followers : 6350
- following : 969
tiktok:
- url : https://tiktok.com/@sawaync
- username : sawaync
- bio : Quia ipsa facere voluptatem placeat qui non repudiandae.
- followers : 4892
- following : 357