Secure IoT SSH Access: AWS Setup Guide [Step-by-Step]
Can you truly unlock the potential of your IoT devices from anywhere in the world? Yes, you can establish a secure and reliable connection to your IoT devices over the internet using Amazon Web Services (AWS), transforming the way you manage and interact with your remote infrastructure.
Remote SSH access to IoT devices is becoming increasingly critical in todays interconnected landscape. Whether you're a developer, a system administrator, or a tech enthusiast, the ability to securely connect to and manage these devices remotely is no longer a luxury, but a necessity. Secure Shell (SSH) provides a secure means of connecting to devices, executing commands, and transferring files securely, making it an indispensable tool in the IoT world. By integrating SSH with the robust capabilities of AWS, you can create a powerful and scalable solution for managing your IoT devices.
| Concept | Secure Remote Access for IoT Devices |
| Technology | SSH (Secure Shell) and AWS (Amazon Web Services) |
| Primary Function | Enables secure and remote access, management, and control of IoT devices over the internet. |
| Key Components | AWS IoT Core, EC2 (if applicable), IAM (Identity and Access Management), SSH Clients/Servers. |
| Benefits | Increased security, scalability, accessibility, and simplified device management. |
| Reference Website | AWS IoT Core |
Setting up remote SSH IoT access over the internet with AWS involves a few key steps, but don't worry, the process is manageable. AWS offers a secure and scalable platform, integrating services like AWS IoT Core, EC2 (if needed), and IAM to facilitate SSH access. This approach enhances both security and efficiency. Remember, the objective is to ensure a robust and reliable connection to your IoT devices, and AWS offers the tools to achieve this.
- Unveiling Kristi Noem From Bedhead To Bikini Buzz Latest Updates
- Alice Rosenblum Updates Leaks Whats Trending Now
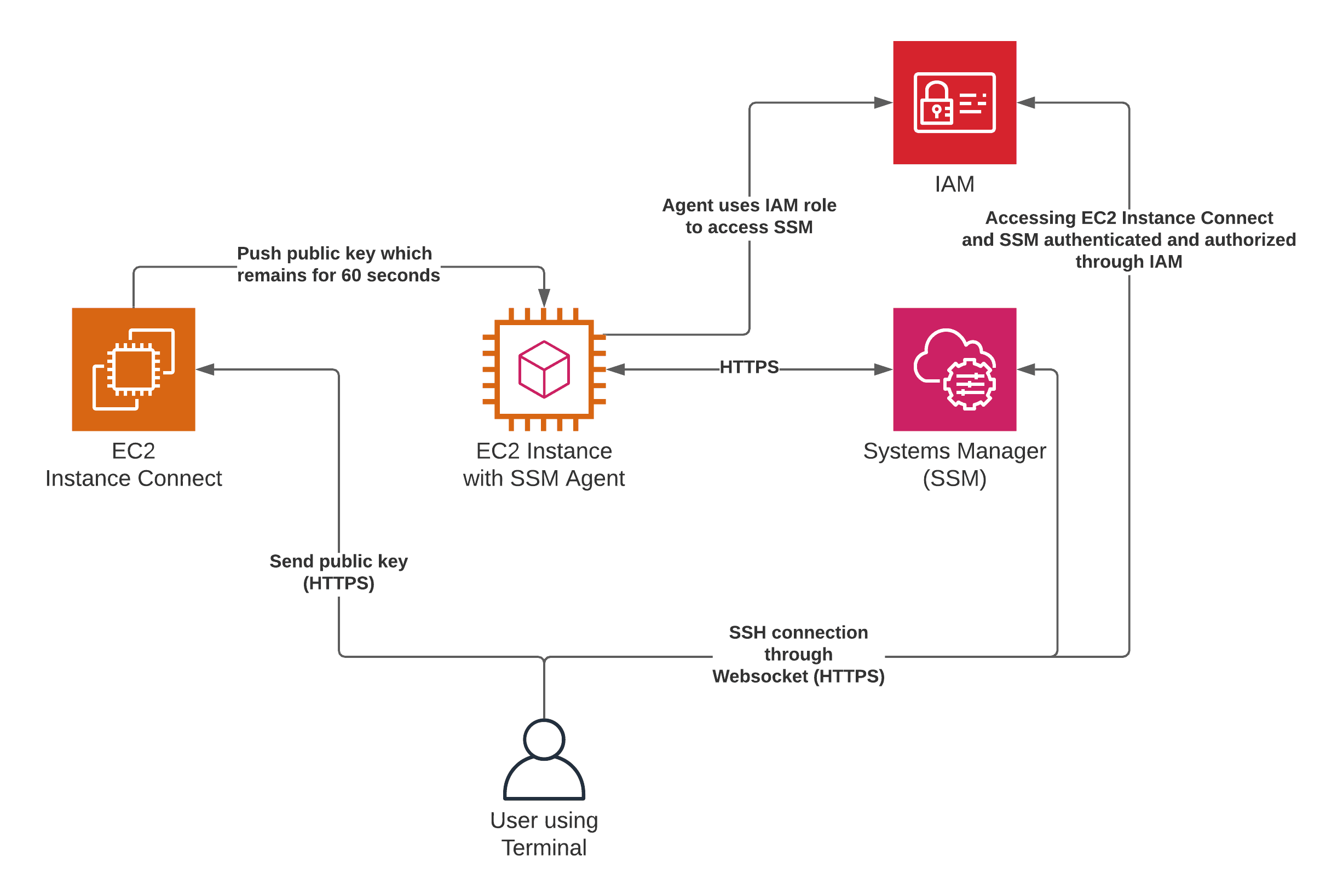
The quick setup method provides a streamlined way to rotate access tokens and SSH into the remote device directly within a web browser. To leverage this feature, you must first create an IoT thing within the AWS IoT registry; for example, we might name it "remotedevicea". This "thing" represents your remote device in the cloud. To open a new tunnel using this method, you utilize the `opentunnel` API operation. However, its important to note that creating a tunnel via the quick setup method is exclusively available through the AWS IoT console. If you prefer using the AWS IoT API reference or the AWS CLI, youll need to utilize the manual setup method, which grants greater control and flexibility, but with a steeper learning curve.
AWS IoT Core is the heart of AWS's IoT offerings. It is a managed cloud service that allows you to connect, manage, and secure your IoT devices at scale. Secure tunneling is a feature within AWS IoT Device Management. It helps customers access remote devices over a secure connection, all managed by AWS IoT. A significant advantage of secure tunneling is that it does not require updates to your existing inbound firewall rules. Therefore, you can maintain the same security level provided by your firewall rules at the remote site. This design element streamlines the setup and minimizes potential security vulnerabilities.
One of the most effective ways to remotely access and manage IoT devices is through SSH over the internet using AWS. AWS provides robust tools to manage and connect IoT devices remotely without exposing them to public IPs. By integrating AWS IoT Core with SSH, you can establish a secure connection between your IoT device and the AWS cloud.
- Unveiling Aagmaalmen Details Competitors Amp Insights In 2025 Google Discover
- Alice Rosenblum Onlyfans Lawsuit Latest News Updates
Now, let's delve into the practical aspects of setting up this remote SSH access. Connecting an SSH IoT device over the internet using AWS on Windows might initially seem like a challenge, but with the right guidance, it's entirely achievable. From setting up your Windows environment to configuring AWS and generating SSH keys, each step will bring you closer to a secure and functional IoT setup. Before you begin, ensure you've created an IoT thing (for example, "remotedevice1") in the AWS IoT registry. This "thing" serves as the cloud-based representation of your remote device.
The journey of connecting SSH IoT devices over the internet using AWS starts with understanding the core principles. Remote SSH IoT over the internet is essentially the process of securely accessing and managing IoT devices remotely via SSH protocols. SSH, often referred to as the "swiss army knife" of remote access tools, allows you to connect to devices, execute commands, and transfer files securely. In today's interconnected world, learning how to connect SSH IoT devices over the internet using AWS on Windows has become essential for developers, engineers, and tech enthusiasts. With the rapid growth of IoT technology, managing and securing remote devices has never been more critical.
When it comes to connecting SSH IoT devices over the internet using AWS on Windows, AWS has everything you need to simplify the process. AWS offers several advantages for IoT SSH connections, including the ability to scale to meet the demands of your IoT devices. Key AWS services that will help you connect your IoT devices include AWS IoT Core, which acts as the central hub, and options like EC2, depending on your specific setup requirements.
AWS IoT Core is a managed cloud service that enables secure, bi-directional communication between your IoT devices and the cloud. It provides features like device authentication, authorization, and message routing, forming the foundation for your remote SSH setup. By integrating AWS IoT Core with SSH, you can create a secure channel for accessing and managing your devices. This is the heart of AWSs IoT offerings, providing the infrastructure needed to connect, manage, and secure your IoT devices.
The manual setup method, while more involved, offers greater control. It involves configuring the AWS IoT Core, setting up the necessary security certificates, and establishing the SSH connection. The quick setup method, accessible through the AWS IoT console, simplifies the process, particularly for initial testing and rapid deployments. The choice between the two depends on your project's specific requirements and your level of experience with AWS services.
The process involves several key steps. First, you will need to create an IoT thing in the AWS IoT registry. This "thing" represents your physical device in the AWS cloud. Next, you'll need to configure the necessary security certificates and policies to ensure secure communication. After that, you'll need to configure your device to connect to AWS IoT Core. With these components in place, you can establish a secure SSH connection to your device over the internet.
AWS provides robust tools for managing and connecting IoT devices remotely, without exposing them to public IPs. AWS infrastructure can scale to meet the demands of your IoT devices, ensuring performance and reliability, no matter the size of your deployment. The integration of services like AWS IoT Core, EC2, and IAM provides a secure and scalable solution. The benefits of using AWS for IoT SSH connections are significant, including enhanced security, scalability, and simplified device management. By adopting this approach, you can significantly streamline your IoT device management, while simultaneously enhancing security and operational efficiency.
With the increasing adoption of IoT devices, ensuring secure communication has become paramount. Remote access to IoT devices is no longer a luxury; it is a necessity. Together, SSH and AWS create a powerful combination for securely accessing IoT devices over the internet. This guide has walked you through the process of setting up and securing IoT SSH over the internet using AWS, ensuring a robust and reliable connection. Whether youre a developer, system administrator, or tech enthusiast, this information will empower you to securely manage your IoT devices from anywhere in the world.

![How to Access IoT Devices Remotely with SSH [6 Easy Steps] cloud](https://cloud.lavainfo.my.id/wp-content/uploads/2024/10/Access-IoT-Devices-Remotely-Using-SSH.webp.webp)
Detail Author:
- Name : Buster Hudson
- Username : rjohnston
- Email : wyman.gabriel@yahoo.com
- Birthdate : 2001-03-06
- Address : 8878 Adah Light Suite 866 East Eldachester, NC 00252-6609
- Phone : (281) 769-4304
- Company : Wuckert-Moen
- Job : Agricultural Sales Representative
- Bio : Asperiores voluptates nobis magnam ut autem cum. Quo vel quos rerum.
Socials
instagram:
- url : https://instagram.com/ctorphy
- username : ctorphy
- bio : Rerum quibusdam aut in. Dolores dicta culpa vitae rerum omnis. Voluptatem enim qui ut quis.
- followers : 1391
- following : 664
facebook:
- url : https://facebook.com/candidotorphy
- username : candidotorphy
- bio : Impedit dolores illum non iure molestiae dolores.
- followers : 1893
- following : 704
twitter:
- url : https://twitter.com/torphy1992
- username : torphy1992
- bio : Iure voluptatem earum distinctio et. Voluptas et incidunt nisi esse aliquid quis.
- followers : 5270
- following : 2581
tiktok:
- url : https://tiktok.com/@candido2246
- username : candido2246
- bio : Illum reiciendis at sapiente magni enim.
- followers : 4777
- following : 2239