IoT SSH: Secure Remote Access & Management - Best Apps Compared
Are you ready to unlock the full potential of your Internet of Things (IoT) projects while fortifying them against cyber threats? The integration of Secure Shell (SSH) into IoT applications is not merely a trend; it's a fundamental shift towards secure, manageable, and scalable device management in an increasingly interconnected world.
The realm of IoT is expanding at an unprecedented rate. From smart homes and industrial automation to healthcare and transportation, the number of connected devices continues to surge. This rapid growth introduces complex challenges in securing these devices and ensuring their efficient management. SSH, with its robust security features and remote access capabilities, emerges as a crucial component in addressing these challenges.
At its core, SSH provides a secure channel for communication between devices and their controlling systems. It employs encryption to protect data in transit, preventing unauthorized access and mitigating the risk of data breaches. SSH also offers secure remote access, allowing administrators to manage and control IoT devices from any location with an internet connection. Furthermore, it facilitates the secure transfer of files and the execution of commands, streamlining device maintenance and troubleshooting.
- Kristi Noem Bikini Photo Viral Buzz Reactions
- Supernanny Jo Frost Career Family Life Darrin Jackson Details
In this comprehensive exploration of IoT SSH applications, we will delve into their significance, applications, and the crucial role they play in the broader IoT landscape. We will analyze the key criteria for selecting the best SSH tools and highlight the security features that are paramount in protecting your connected devices. We will also examine the best practices for implementing SSH in your projects and discuss the endless possibilities that this technology unlocks.
Let's examine the core functionalities that make SSH an indispensable tool in the IoT domain. SSH provides a secure method for remote access, allowing administrators to connect to IoT devices from anywhere with an internet connection. It offers secure remote device management, enabling configuration, updates, and troubleshooting without physical access. Moreover, SSH facilitates secure communication, enabling the transfer of data between devices and their controlling systems. Additionally, SSH supports secure file transfer, which is essential for exchanging data, configurations, and software updates.
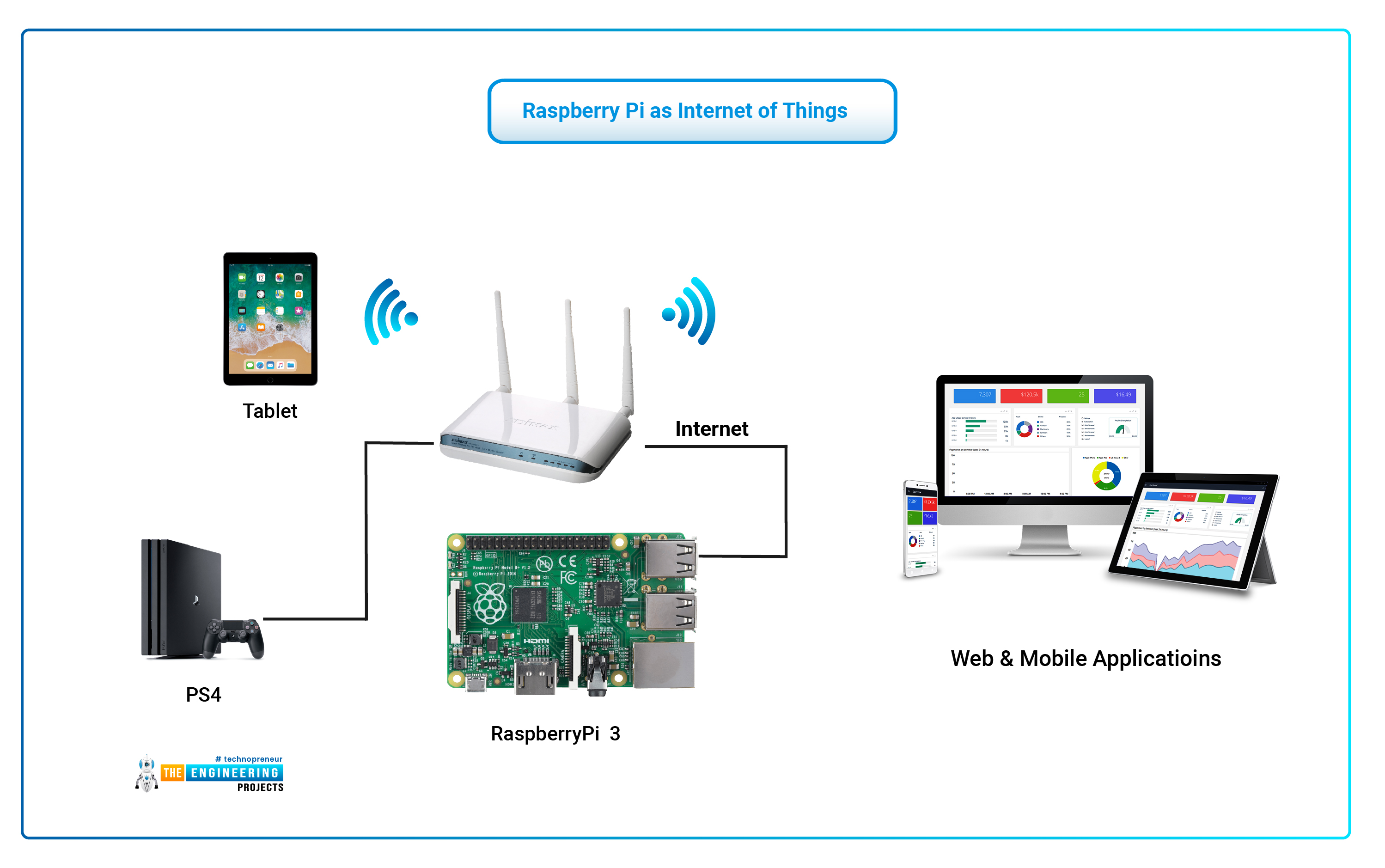
Now, lets consider some practical applications of SSH in the IoT world. Remote monitoring and control of machinery from any location is a primary use case. SSH enables secure access to industrial equipment, allowing operators to monitor performance, diagnose issues, and perform maintenance remotely, thereby increasing efficiency and reducing downtime. SSH also plays a crucial role in managing home automation systems without sacrificing security. Homeowners can remotely control and monitor their smart devices, ensuring the security of their home environment. Furthermore, SSH is used in the smart grid, providing secure remote access to smart meters and other devices, enabling utilities to monitor and manage energy consumption and distribution efficiently.
The growing sophistication of IoT ecosystems necessitates the implementation of robust security measures. This is where IoT SSH applications come into play. They provide a robust layer of security for remote access and management of IoT devices. By implementing SSH with robust security features, organizations can significantly reduce the risk of data breaches and associated costs. Understanding the role of SSH in IoT is essential for anyone looking to harness the full potential of this technology while ensuring data protection and system integrity.
As the number of connected devices increases, ensuring secure communication and remote access is essential. This is where the comparison of IoT SSH applications becomes crucial. Comparing these applications helps you make an informed decision based on your specific needs. A comparison of the top IoT SSH applications is given below in the table.
Here's a detailed comparison of popular IoT SSH applications, designed to empower you in making informed decisions based on your project's unique demands:
| Application | Key Features | Security Measures | Ease of Use | Scalability | Use Cases |
|---|---|---|---|---|---|
| OpenSSH | Industry-standard SSH implementation, widely used, versatile, and open-source. | Strong encryption, key-based authentication, customizable security settings. | Command-line interface, requires some technical expertise. | Highly scalable, suitable for a large number of devices. | Remote access, secure file transfer, remote command execution. |
| Dropbear SSH | Lightweight SSH server designed for resource-constrained devices. | Supports key-based authentication, strong encryption. | Easy to install and configure on embedded systems. | Well-suited for devices with limited resources. | Embedded systems, routers, and other resource-constrained devices. |
| PuTTY | Free and open-source SSH client for Windows, easy to use. | Supports various encryption algorithms, key-based authentication. | User-friendly graphical interface. | Suitable for individual users and small-scale deployments. | Remote access, secure file transfer, terminal access. |
| Bitvise SSH Client | Feature-rich SSH client for Windows, supporting various protocols. | Supports strong encryption, key-based authentication, and port forwarding. | User-friendly interface, with advanced options. | Suitable for both personal and commercial use. | Remote access, secure file transfer, tunneling. |


Detail Author:
- Name : Blaise Hill
- Username : robel.roselyn
- Email : kuphal.eden@hotmail.com
- Birthdate : 1972-03-04
- Address : 6891 Russell Unions West Lolitaberg, CT 85434
- Phone : 1-502-764-2432
- Company : Bednar LLC
- Job : Landscape Architect
- Bio : Eaque quas cum architecto voluptates reprehenderit. Cum autem laudantium accusamus ex.
Socials
linkedin:
- url : https://linkedin.com/in/dannie.bechtelar
- username : dannie.bechtelar
- bio : Nulla eius sunt praesentium et velit.
- followers : 3408
- following : 889
tiktok:
- url : https://tiktok.com/@dannie_official
- username : dannie_official
- bio : Expedita eligendi mollitia quia enim.
- followers : 6938
- following : 2419
facebook:
- url : https://facebook.com/dannie.bechtelar
- username : dannie.bechtelar
- bio : Reiciendis voluptatum qui odio aut consequuntur voluptatum fuga.
- followers : 2280
- following : 1053
instagram:
- url : https://instagram.com/dbechtelar
- username : dbechtelar
- bio : Tenetur sunt autem non labore rerum. Incidunt id ab tempore amet sapiente.
- followers : 565
- following : 2348
twitter:
- url : https://twitter.com/dannie_id
- username : dannie_id
- bio : Quis molestiae recusandae atque commodi nam praesentium. Suscipit maxime ullam ipsum nostrum enim aspernatur ut. Magni cupiditate et aut rerum.
- followers : 3517
- following : 1011