AWS IoT SSH Access: Secure Remote Device Management
Is securing remote access to your Internet of Things (IoT) devices a persistent challenge? Navigating the complexities of remote access to IoT devices, particularly those shielded by firewalls and public IP addresses, demands robust solutions.
The ability to reach these devices remotely is crucial for various tasks, including management, firmware updates, and health monitoring. Traditional methods often fall short, leading to vulnerabilities and operational inefficiencies. Fortunately, cloud platforms like Amazon Web Services (AWS) provide comprehensive tools and services designed to streamline and secure this process. This article delves into the specifics of establishing secure Shell (SSH) access to IoT devices using AWS, offering detailed insights for both newcomers and seasoned professionals.
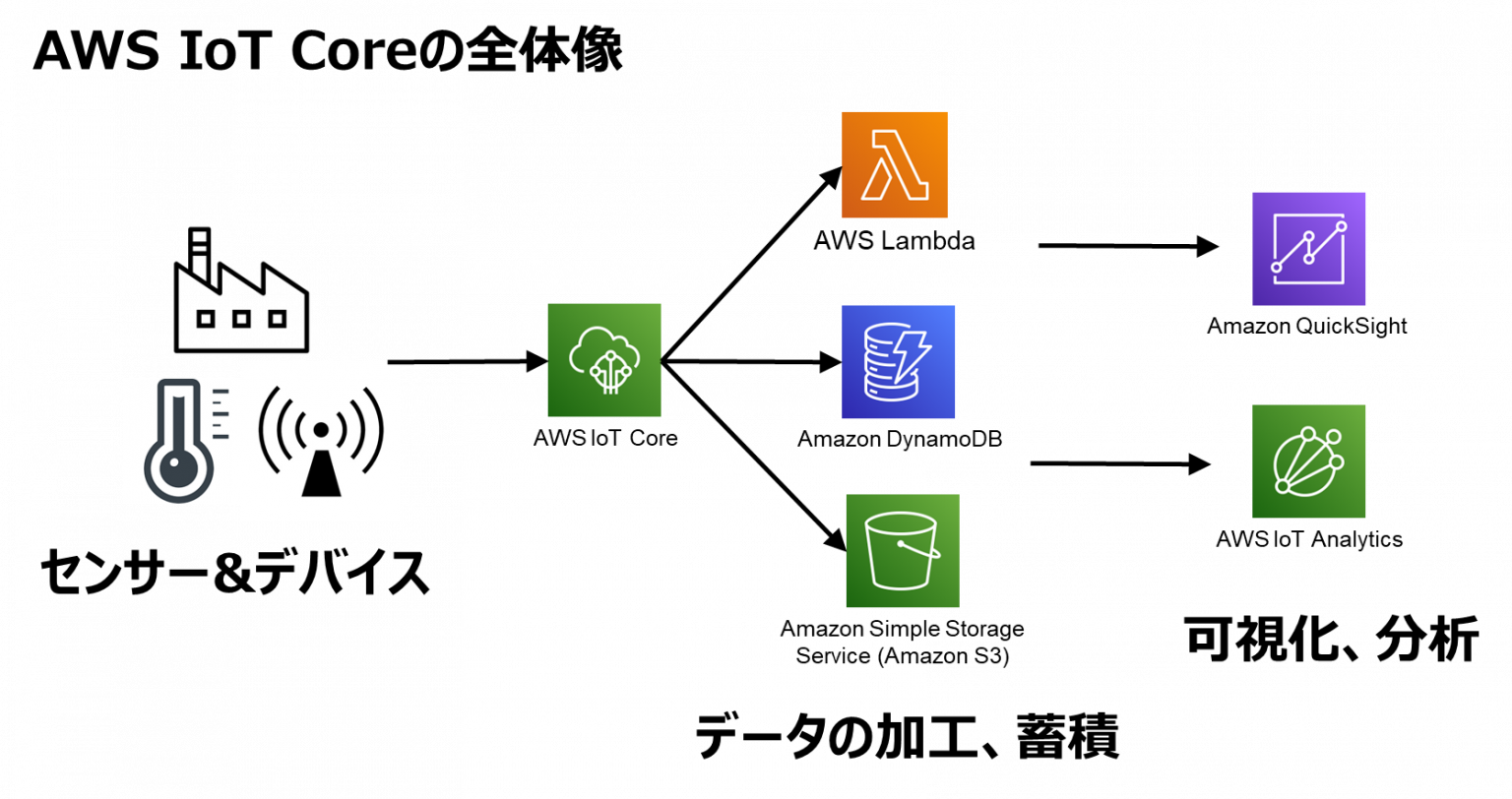
Consider a common scenario: you have an IoT device agent running on a remote device. This agent establishes a connection with the AWS IoT Device Gateway and subscribes to an MQTT topic. This setup forms the foundation for remote communication. Beyond this basic connection, AWS provides a suite of services that enhance the security, scalability, and efficiency of IoT operations. These services act as a central hub for your IoT devices, allowing them to communicate securely with the cloud. Managing device fleets, updating firmware, and monitoring device health all become manageable through a single, unified dashboard.
To understand the mechanics, one can consider the steps involved in setting up Ubuntu on AWS for SSH access to your IoT device. This involves configuring an AWS instance with Ubuntu, and then securing the environment by enabling SSH access. This setup allows you to remotely manage your IoT devices, streamlining operations and enhancing security. AWS also provides the option of using the quick setup method to rotate the access tokens and SSH into the remote device within the browser.
Secure tunneling is another powerful feature. It offers a secure, remote access solution integrated directly with AWS IoT. With this, you can access your IoT devices remotely from anywhere, negating the need for updating existing inbound firewall rules. With AWS services like AWS IoT Core, AWS Systems Manager, and AWS CloudFormation, you can build a robust infrastructure for managing IoT devices remotely. AWS provides the infrastructure and tools to make this process smooth and secure. From setting up your environment to managing your devices, AWS has got you covered.
Whether you're a developer, system administrator, or IT professional, the nuances of IoT remote access with SSH on AWS enhance your ability to manage and secure IoT devices effectively. The following table presents a comparative analysis of different methods of IoT device access:
- Kristi Noem From Cowgirl Outfits To Political Career
- Alice Rosenblum Uncensored Content Onlyfans Leaks 2024
| Method | Description | Pros | Cons | Use Case |
|---|---|---|---|---|
| SSH with VPN | Uses a VPN to create a secure network connection, then SSH is used. | Relatively secure, widely understood. | Requires VPN setup, can be complex. | Accessing devices within a private network. |
| SSH with Proxy | Uses a proxy server to forward SSH traffic. | Bypasses firewall restrictions, simpler setup than VPN. | Proxy server is a single point of failure, less secure. | Accessing devices in a restricted network. |
| AWS IoT Secure Tunneling | Uses AWS IoT services to create a secure tunnel for SSH. | Highly secure, easy integration with AWS IoT, no firewall changes required. | Requires AWS IoT setup, may have associated costs. | Remote access to devices managed by AWS IoT. |
| Direct SSH | Direct SSH connection to a device with a public IP. | Fast, straightforward. | High security risk, vulnerable to attacks, requires public IP. | Testing, debugging in a controlled environment. |
These options offer varying degrees of complexity and security, with the AWS IoT Secure Tunneling emerging as a modern and secure approach.
Using SSH to access your IoT devices remotely offers numerous advantages. It provides a secure and encrypted channel for communication, ensuring that data transmitted between your device and your management system is protected. SSH access allows for comprehensive device management, including the ability to update software, configure settings, and diagnose issues. In 2023, there are many tools available to streamline setup of IoT devices that support configuration and access. AWS offerings provide a range of IoT solutions, however, those not on AWS can take a more traditional approach by using SSH with a VPN or proxy connection.
Mastering SSH control is critical for secure connectivity. You'll need a few key tools: the web interface for managing your AWS resources, a tool for connecting to your EC2 instance and IoT devices (like PuTTY or OpenSSH), and a set of cryptographic keys for authentication.
The foundation lies in setting up SSH on your IoT devices. This includes configuring your device's operating system to accept SSH connections and ensuring the security of your device is maintained. To begin, configure an AWS instance, which typically involves setting up an EC2 instance in your AWS account and installing an operating system such as Ubuntu.
To delve further, consider the following points:
- Understanding SSH: Secure Shell (SSH) is a cryptographic network protocol used for secure access to a device. It provides a secure channel over an unsecured network.
- AWS IoT Core: AWS IoT Core is a managed cloud service that lets connected devices easily and securely interact with cloud applications and other devices.
- Benefits of AWS: AWS provides the infrastructure, services, and tools to streamline the management of IoT devices.
By integrating SSH access with AWS, you enhance security, scalability, and efficiency of your IoT operations. AWS offers a suite of tools and services that enable developers and system administrators to manage IoT devices effectively. SSH, as a cryptographic network protocol, is essential for secure access to devices. This is a powerful combination because AWS provides a robust ecosystem for IoT deployments, including services like AWS IoT Core. By integrating SSH, users can remotely manage devices, troubleshoot issues, and perform secure updates.
For those considering the AWS route, why choose AWS for IoT SSH access? AWS is a leading cloud provider offering a comprehensive suite of tools for managing IoT devices. This leads to a seamless integration of all your devices.
In conclusion, accessing IoT devices through SSH on AWS offers numerous benefits, including enhanced security, scalability, and automation. By following the guidelines, organizations can successfully implement and manage IoT SSH deployments that meet their unique requirements. The choice of AWS offers a robust platform for IoT device management, with SSH access playing a crucial role in secure communication.

Detail Author:
- Name : Kristoffer Cole
- Username : pherman
- Email : eula19@ohara.net
- Birthdate : 1981-07-14
- Address : 771 Hermann Mountains Apt. 129 Lake Luigitown, ND 23006
- Phone : 270-819-8115
- Company : Kiehn-Wisoky
- Job : Ambulance Driver
- Bio : Rerum eum ad cum ex iste. Praesentium amet rerum hic tempora sed voluptatem necessitatibus. Ducimus soluta et ut quos eum voluptate. Itaque magnam accusamus at et aspernatur.
Socials
instagram:
- url : https://instagram.com/ezra4843
- username : ezra4843
- bio : Ut debitis rerum ut voluptates ut nihil. Qui animi corporis placeat expedita.
- followers : 2022
- following : 408
facebook:
- url : https://facebook.com/ewilkinson
- username : ewilkinson
- bio : Voluptatem dolores sapiente eaque suscipit molestiae.
- followers : 6558
- following : 1385