AWS IoT Secure Tunneling: SSH Access To Your Devices Made Easy
Can you remotely access and manage your Internet of Things (IoT) devices securely, regardless of their location and the firewalls they may be behind? The ability to establish secure SSH tunnels using AWS IoT Core offers a powerful solution, streamlining device management and significantly reducing operational costs.
The digital landscape has undergone a dramatic transformation, with IoT devices becoming increasingly prevalent across various industries. From smart home appliances to industrial sensors, these devices generate vast amounts of data and provide valuable insights. However, the distributed nature of these devices often poses a significant challenge: how to securely access and manage them remotely, especially when they are behind firewalls that restrict inbound traffic. This is where the concept of secure tunneling comes into play, and AWS IoT Core offers a compelling solution to this problem.
Using firewalls is a common way to protect and secure access to IoT devices. Yet, its challenging to access and manage devices deployed at remote sites, behind firewalls that block all inbound traffic. Troubleshooting devices can involve sending technicians onsite to connect to those devices. This increases the complexity and the cost of device management. With its powerful services, AWS makes it easy to secure and scale remote access for your IoT devices. AWS IoT Core acts as the backbone of your IoT infrastructure, enabling seamless communication between devices and the cloud.
| Aspect | Details |
|---|---|
| Key Concept | Secure SSH Tunneling with AWS IoT Core |
| Description | Enables secure, bidirectional communication to remote devices over a connection managed by AWS IoT, bypassing the need for inbound firewall rule modifications. |
| Core Components | AWS IoT Core, AWS IoT Device SDK, SSH (Secure Shell) Protocol |
| Benefits |
|
| Common Use Cases |
|
| Technologies Involved | AWS IoT Core, AWS Systems Manager, AWS CloudFormation, SSH Protocols, MQTT, Firewall Configuration |
| Relevance | Crucial for secure remote device management in modern IoT deployments, especially when dealing with devices behind firewalls. |
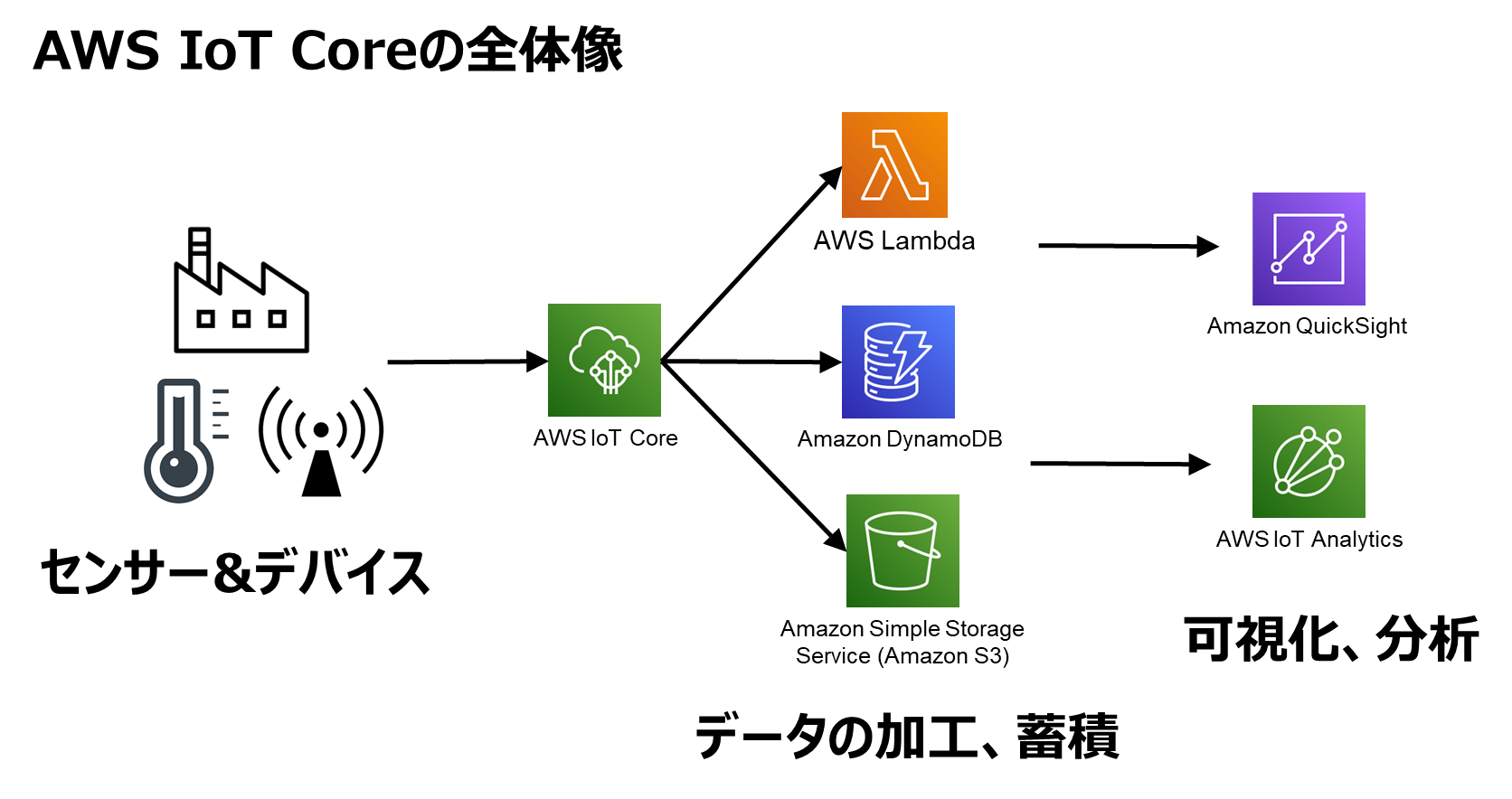
At the heart of this solution is AWS IoT Core, a managed cloud service that allows you to securely connect, manage, and interact with your IoT devices. It acts as a central hub, enabling seamless communication between devices and the cloud. This service provides features such as device authentication, secure data transfer, and device management capabilities. By leveraging AWS IoT Core, you can build a robust infrastructure for managing IoT devices remotely. With this, you can manage device fleets, update firmware, and monitor device healthall from a single dashboard.
One of the core functionalities offered by AWS IoT Core is secure tunneling. This feature allows you to establish a secure, bidirectional communication channel to your remote devices. Essentially, it creates a secure tunnel through which you can access your devices, even if they are behind firewalls that block inbound traffic. Secure tunneling does not require updates to your existing inbound firewall rules, so you can keep the same security level provided by firewall rules at a remote site. Using this method, you can rotate the access tokens and SSH into the remote device within the browser. You can open a secure tunnel using the AWS Management Console, the AWS IoT API reference, or the AWS CLI.
The setup involves several key steps. Firstly, you'll need to create an IoT thing in the AWS IoT registry, which represents your remote device in the cloud. This "thing" will act as the digital twin of your physical device, allowing you to manage and interact with it remotely. To open a tunnel using the quick setup method, you must have created an IoT thing (for example, remotedevicea) in the AWS IoT registry. Secondly, you'll need to set up an IoT device agent on the remote device. This agent connects to the AWS IoT device gateway and is configured with an MQTT topic subscription. The source is typically where you want to initiate the SSH connection from (in this case, AWS), and the destination is the device you want to connect to (your macbook).
- Alice Rosenblum Tiktok Leaks Onlyfans What You Need To Know
- Alice Rosenblum Exclusive Content Leaks What You Need To Know
This process typically involves the following steps: Upon creating the tunnel using IoT Core, you receive the access tokens for source and destination. Connecting a device to AWS IoT Core by using the AWS IoT Device SDK, the tutorials in this section focus on creating a tunnel using the AWS Management Console and the AWS IoT API reference. In the AWS IoT console, you can create a tunnel from the tunnels hub page or from the details page of a thing that you created. With this AWS IoT managed tunnel, you can open the SSH connection needed for your device.
With AWS services like AWS IoT Core, AWS Systems Manager, and AWS CloudFormation, you can build a robust infrastructure for managing IoT devices remotely. This service acts as a central hub for your IoT devices, allowing them to communicate securely with the cloud. For more information about using AWS IoT secure tunneling to connect to remote devices, see AWS IoT secure tunneling in the AWS IoT developer guide.
| Service | Function |
|---|---|
| AWS IoT Core | Acts as the backbone of your IoT infrastructure, enabling seamless communication between devices and the cloud. Manages device identity, authentication, and authorization. Provides secure, bi-directional communication via MQTT. |
| AWS Systems Manager | Allows remote device management, including the ability to run commands, update firmware, and monitor device health. Integrates with AWS IoT Core for secure remote access. |
| AWS CloudFormation | Enables the automation of infrastructure deployment. Simplifies the setup and management of AWS resources for IoT devices. |
| AWS IoT Device SDK | Provides the necessary libraries and tools to enable devices to connect to AWS IoT Core. Includes support for secure communication and MQTT. |
The process of establishing an SSH tunnel involves the use of access tokens, which are essential for secure authentication and authorization. These tokens act as digital credentials, verifying the identity of the source and destination devices. You can use the quick setup method to rotate the access tokens and SSH into the remote device within the browser. The source is typically where you want to initiate the SSH connection from (in this case, AWS), and the destination is the device you want to connect to (your macbook). The access tokens are typically provided when you create the tunnel using IoT Core.
To implement secure tunneling, you can use the AWS Management Console, the AWS IoT API reference, or the AWS CLI. The AWS Management Console provides a user-friendly interface for creating and managing tunnels. The AWS IoT API reference offers detailed documentation and APIs for programmatic tunnel creation and management. The AWS CLI provides a command-line interface for automating the process. You can optionally configure a destination name, but it's not required for this tutorial. It is important to note that you must have created an IoT thing (for example, remotedevicea) in the AWS IoT registry. This "thing" corresponds to the representation of your remote device in the cloud.
The quick setup method allows you to rotate the access tokens and SSH into the remote device within the browser. In the AWS IoT console, you can create a tunnel from the tunnels hub page or from the details page of a thing that you created. You can open a secure tunnel using the AWS management console, the AWS IoT API reference, or the AWS CLI. Upon creating the tunnel using IoT Core, i receive the access tokens for source and destination. This is where the power of AWS IoT Core shines, providing a managed service that handles the complexities of establishing and maintaining the tunnel. The quick setup method is designed to simplify the process, making it easier to get started with secure remote access.
If you encounter difficulties while configuring your device for AWS IoT, you might try one of the other device options as an alternative, such as create a virtual device with Amazon EC2 or use your Windows or Linux PC or Mac as an AWS IoT device. This opens up new possibilities for troubleshooting and maintaining these devices. By providing a reliable method of remote access, AWS IoT Core significantly reduces the need for physical intervention, lowering both costs and the time required for maintenance. This is particularly valuable in scenarios where devices are deployed in hard-to-reach locations or where on-site technical expertise is limited.
Enabling SSH on your raspberry pi to remotely connect to it is also a part of the process to establish secure tunneling. For more information, see SSH (secure shell) in the Raspberry Pi documentation. It streamlines the process and makes it more user-friendly. Whether you're managing a handful of devices or a large fleet, the AWS IoT Core service provides the necessary tools and infrastructure to ensure secure, reliable, and scalable remote access.
One significant advantage of using AWS IoT Core for secure tunneling is that it doesn't require changes to your existing inbound firewall rules. Secure tunneling does not require updates to your existing inbound firewall rules, so you can keep the same security level provided by firewall rules at a remote site. AWS makes it easy to secure and scale remote access for your IoT devices. The ability to bypass firewall restrictions makes it ideal for scenarios where devices are deployed in environments with stringent security policies. This ensures that your remote access solution does't compromise your existing security infrastructure.


Detail Author:
- Name : Johnathon Spinka III
- Username : lonnie75
- Email : xromaguera@kuphal.com
- Birthdate : 1990-11-08
- Address : 135 Ankunding Mill Kulasville, NJ 43464-2617
- Phone : (323) 460-4671
- Company : Wiza Group
- Job : Nursery Manager
- Bio : Voluptas saepe sed rem nobis veniam. Maxime sit quaerat sed officiis cum molestiae pariatur expedita. Non beatae dignissimos dolores sed sunt in. Atque quisquam magnam explicabo soluta.
Socials
linkedin:
- url : https://linkedin.com/in/kunze1996
- username : kunze1996
- bio : Est similique asperiores tempore veritatis.
- followers : 2186
- following : 1639
instagram:
- url : https://instagram.com/ottilie_real
- username : ottilie_real
- bio : Inventore nulla tenetur iste impedit aperiam labore. Occaecati officiis et reprehenderit quo quia.
- followers : 1910
- following : 941
facebook:
- url : https://facebook.com/okunze
- username : okunze
- bio : Possimus placeat itaque quos autem et in.
- followers : 4384
- following : 1421
tiktok:
- url : https://tiktok.com/@ottilie168
- username : ottilie168
- bio : Autem nobis corrupti ut alias non debitis.
- followers : 4894
- following : 2429